Here’s a recent e-mail that shows how spammers try to subvert digital controls.
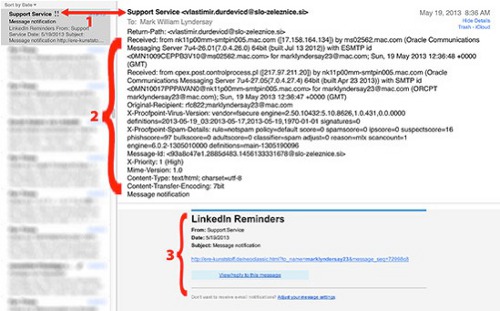
In 1, the sender’s e-mail address is given an official sounding title, but the e-mail client reveals the actual sender, who is not e-mailing from an official LinkedIn account. This field, where users will normally put their real names, can be anything, including another e-mail address entirely and some clients will show that and not the underlying e-mail address as seen at left.
The extended e-mail header is revealed in 2, which tells the truth about the e-mail. A skilled mail server wrangler can read this geek stream and divine a great deal about this e-mail’s routing.
For 3, the sender has spent a bit of effort making the body of their e-mail look like an official LinkedIn transmission, albeit with a link that looks nothing like something that the social media service would use.
Regardless of which side of the political divide you choose to support, it’s clear that the discussions about the recent revelation of a thread of e-mail conversations offered in Parliament by Opposition Leader Dr Keith Rowley has provoked strong emotional reactions.

That’s understandable when it comes to politics, but such sentiments are wholly out of place when it comes to the technologies underlying even such commonplace services as e-mail transmissions.
Technology is absolute. It deals in verifiable bits that either are or are not. A message either has a proper transmission header or it doesn’t. If it doesn’t, it’s unverifiable and useless as evidence, regardless of who offers it.
This may be a confusing matter for politicians, who trade in mood, feelings and allegiances, none of which have any impact on bits.
Information on the web may have mood and feeling, but its existence is trackable and verifiable every step of the way (unless people take the trouble to use anonymizers and other identity obscuring tools).
E-mails can’t just look right or wrong, they are either truly electronic transmissions and can be verified as such with a trackable footprint or they are not. It really is as simple as that.
Editor’s Note: Please read the conclusion to Mark Lyndersay’s blog at his bitdepth website by clicking here
Mark Lyndersay is the editor of technewstt.com, a contributor to TT Newsday and OpEd editor of trinigoodmedia.com. His photography can be found at lyndersaydigital.com.
 Wired868 Wired868 for smart sport news and opinion
Wired868 Wired868 for smart sport news and opinion







Went to the link provided. Very informative.Thank you.